Introduction
Last year I tried running Fedora on a MacBook Pro (Intel i5 processor) to see how much pain was involved in switching to Linux completely. I was also interested to see whether using virtual machines for day-to-day tasks was feasible, via Oracle’s VirtualBox. In the end I didn’t make the switch: an idle guest machine ran at around 20% of host CPU utilisation and so would have consumed too much battery (and, since the fan frequently cut in, would also have run too hot for my liking).
Having recently purchased a Dell XPS 13 – Developer Edition, I thought it would be interesting to try this project again, since the new hardware has a more powerful CPU. Happily, the results are much more promising. I’m recording some of my thoughts to show how I’ve set this up, and to encourage others to give it a try.
Let me first outline what benefits are offered by full desktop virtualisation. Security is the first advantage: if you have a variety of guests for different purposes, malware, viruses or stability issues affecting one will not spread to the others. Commercial software that violates privacy can also be safely contained within the environment in which it is run. Furthermore, if a problem is detected then one can simply roll back to an earlier trusted snapshot, and the issue will be fully reverted.
For example, I am sometimes asked to attend a web-based teleconference that requires Flash. That might be regarded as bad enough (no source code available for review, no manual download process offering checksums) but it then requires an OS-specific commercial binary to be run before the screen-sharing will start. That’s an untrustable vector for potential security/privacy violations, for which the click-through license “agreement” undoubtedly tries to indemnify the corporate author of responsibility. To resolve this, one could simply take a fresh virtual guest, run the untrusted application for the duration of the teleconference, and then rollback or destroy the machine afterwards.
Secondly, virtualisation offers full machine portability. For example, if you set up a guest for web development to run on your laptop, you can shut it down, move it to a desktop machine, and bring it back up again in exactly the same state. With USB3, even large machines can be moved in the time it takes to brew a morning cup of tea, as I note later on.
Thirdly, full machine rebuilds become trivial. On non-virtualised set-ups, operating systems can suffer slow-down and/or crash behaviour as log files are not pared down, registry trees become corrupted, or system packages bloat with age. If the process of reinstalling everything is onerous, rebuilds tend to be put off until they are urgent – but if guests can be shifted to a backup drive, rebuilds are made significantly easier. This also makes swapping the host OS (say from one Linux distro to another) simple enough to do experimentally.
Host installation
The rule of thumb I have used is that there should be as little software on the host as possible. This makes upgrading the host much easier, and reduces the likelihood of introducing security or stability problems into the overall environment. Here’s what I installed:
- Ubuntu 13.10. In retrospect I might have used the Long Term Support version here, to avoid having to rebuild the host every six months. That said, as I mentioned earlier, one of the benefits of full virtualisation is much easier full rebuilds, so I’ll not worry about it just yet!
- VirtualBox 4.3. Oracle offer specific builds for some distributions on their website, including Ubuntu; you can use the version offered in your distro’s software repository, but Oracle’s will be more recent. I recommend always keeping the installer for the last couple of minor versions, so if a new version introduces a problem, downgrading should be easy.
- Tool-bar resource monitor, useful for keeping an eye on CPU usage, which can sometimes be a problem with virtualisation, and I keep an eye on network activity too. I use “indicator-multiload” for this.
- Password storage application. This allows passwords to be stored out of the reach of any malware that might creep into a guest – though most password managers will use strong symmetric encryption anyway.
- Music. I listen to music a lot on the laptop, and it makes sense not to duplicate a collection across each guest (especially since mine is 50G+ and the machine only has 256G to play with!). Presently I am running the Exaile player on the host, though there’s some bugs, so I expect to change that. Guest integration would be nice, so I might perhaps share the music folder with guests on a read-only basis and run a local player instead.
- Static data dumps for guests. I often rsync database dumps to the laptop, and I’ll usually do this from a guest so the correct SSH keys are used, but it’ll write to a folder on the host. This avoids the need to make guest drives much larger, which would complicate backups and rebuilds.
- Drivers for hardware support. You usually don’t want to do hardware-level stuff in the guest, so drivers will generally go on the host. Get all the necessary hardware working at this level first (trackpads, touch-screens, connectivity etc) and it should then work fine inside your guest operating systems.
VirtualBox guest configuration
I’m currently of the view that several virtual machines should be created, split by their intended purpose. For example, I am likely to run “Work development”, “Home development” and “Home general” at various times. Each of these VMs can be configured appropriately to the task in hand. For example, a work development machine would likely have a larger allocation of RAM (the XPS 13 only has 8G of non-upgradeable RAM, but 4G to run LAMP, NetBeans, Firefox, Thunderbird and GIMP in a guest turns out to be ample).
There’s a few features in VirtualBox that are well worth being aware about. Firstly, switch on as much hardware graphics acceleration and CPU virtualisation as you can. It’s also worth allocating a good chunk of RAM for the display, especially if you want to run at high res: I use 128M here. Once everything here is happy, I’ve found window animations (e.g. the workspace switcher) change from painfully sluggish to native speeds (resetting the texture quality via Unity Tweak to “Fast” may have helped here also).
For your disk size, err on the size of caution and make it larger than you think you need (it can be increased later, but it’s fiddly). I’m currently happy with my 60G work machine, and since it is dynamically sized it only takes up as much space as it actually uses. I did try a fixed-size disk (since these are meant to be faster), but when I needed to resize it, I found that VirtualBox forced a conversion to the dynamic type anyway.
For wifi connectivity, leave that to the host and allow guests to use Ethernet emulation. Both distros I’ve tried so far have auto-configured this and worked flawlessly.
I’ve also turned on the bidirectional clipboard. This means anything cut or copied in the host or a guest will be available to all the others, as if they shared one clipboard. If you are extremely security conscious, it’s worth noting that some browser vulnerabilities have allowed malware to peek into the clipboard, but in practice — even if you use it for pasting passwords from a credential manager — I’m not sure the threat is significant.
Lastly, create as many Shared Folders as each guest needs. I’ve read-only ones for music and installers, and a writable one for database dump updates. Obviously, it’s worth creating them only as required, and read-only by default.
Installing guests
Once a guest machine is configured, you can install your operating system of choice. I recommend trying a few here, to see what feels best for you. I’m trying Ubuntu 13.10 and Mint 16 at present: Ubuntu is good but has a few bugs, whereas Mint seems more polished (although I’ve not used it as much). I tried Arch, but its lack of GUI installer put me off going any further (another time, perhaps).
I add the same resource monitor on the task-bar to guests as I use on the host. This allows me to keep an eye on processes that are consuming too much CPU/data, and to restart or replace them as necessary.
For development machines, I use the latest NetBeans binary downloaded directly from the NetBeans website. The repository install can be used, but it will generally be a few versions behind. I’m mildly of the view that version 8.0 is somewhat better with mysterious high CPU consumption, though I suspect the jury is still out at present. As with VirtualBox, I keep the installers for the last two releases to hand, on a read-only shared folder, in case I need to drop back a version. (I’ll discuss the security issues related to downloading software manually later on).
Hardware
I should note a few things about the hardware. I said at the start that I’d tried this experiment on an i5 MacBook Pro, but that I wasn’t convinced by the results. I’m not averse to trying that again (perhaps with a different base OS) but I’m certainly impressed with the results from the i7. The 4-core processor runs most of the time at 10% utilisation and will happily give me 4.5-5.5 hours away from a power socket, so long as a beady eye is kept on Java. I wonder whether the most recent processor-level virtualisation instructions (and perhaps improvements in virtualisation software) have made GUI environments much more practical to virtualise, even on batteries.
One of the interesting challenges in configuring the XPS 13 DE was investigating spurious wake-ups from sleep after closing the lid. It turns out that this behaviour is deliberate (although the failure to go back to sleep again probably isn’t). It’s called Intel Autostart and is intended to periodically wake the machine, connect via a trusted wifi connection, and refresh all remote data sources (such as email and social networking feeds). I doubt Linux supports this, but moreover it sounds like a house-fire waiting to happen, so I’ve turned it firmly off in the BIOS (more info here).
Whilst on the topic of the machine itself, I should say that I really like the XPS 13; Dell have done a really good job here. It’s great to look at, as is the high-gloss high-def screen, the aluminium body and the carbon-fibre base. The ultra-book weight is a joy compared to the bulk of the 15″ MacBook Pro, and whilst there is a trade-off with a smaller viewing pane, it’s not been a problem in practice.
As I said earlier, the battery life is pretty good, and the keyboard offers excellent tactile feedback, and is back-lit too. I’m pleased with the size of the trackpad, but in terms of responsiveness it’s not quite as good as Apple: single-clicks sometimes turn into double-clicks, and at other times a click doesn’t seem to register at all. I have enabled palm detection, but occasionally still get cursor jump when I type. That said, these minor niggles may be driver/configuration issues anyway, so I wouldn’t judge the machine on that basis.
Some people may hesitate to buy this machine on the basis of its 8G RAM limit. Certainly 16G would be nice, but such a model may never be developed, and in any case I’ve not yet overloaded a 4G VM! I am quite willing to believe at this stage (as long as I don’t find a need for parallel guests) that more RAM would just go to waste.
The one area that does cause some dissatisfaction is the on-board wifi module, which frequently detects two bars of strength when the Mac registers full-strength at the same location. This relatively weak hold on connectivity unfortunately results in periodic disconnections that need to be manually reset in the host. I’ve seen other complaints about this on the web, so I suspect a design limitation. To fix this, I might try an external USB wifi dongle; you can get ones now that will sit nearly flush in a USB socket, and need not be removed even in transit.
Usability
Once you’ve set up a good number of usability shortcuts, you can almost forget you’re running in a virtual machine. The only things I need to do in the host are:
- Upgrade the OS
- Start guests
- VirtualBox upgrades and kernel modules
- Connect to wifi
- Make hardware configuration changes
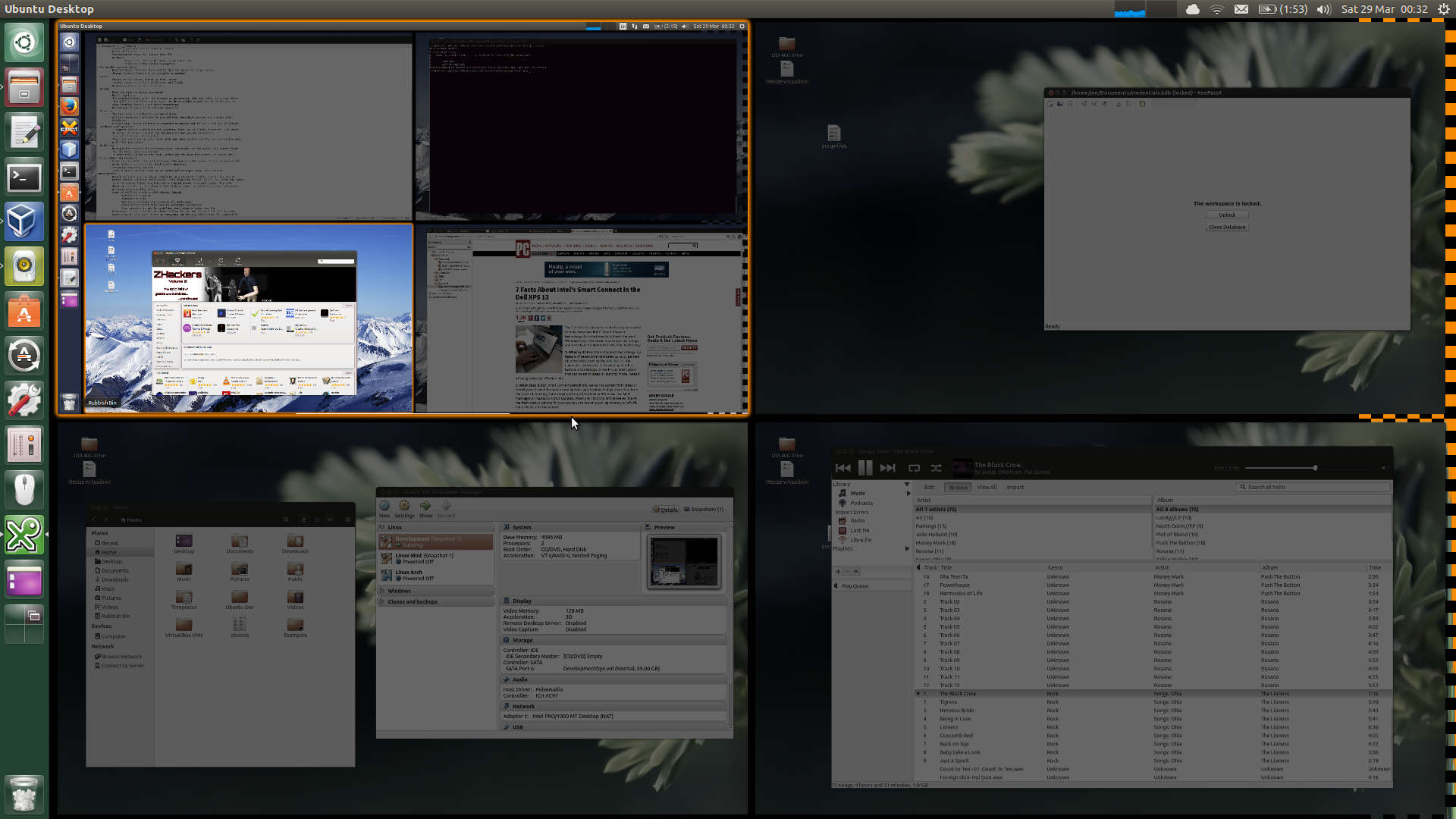
Everything else happens in a guest in full-screen mode. I’m a big fan of workspaces, and I use Ubuntu’s Hotcorners to trigger it. A trackpad flick into the top-right corner activates workspaces on the guest, and a flick into the bottom-left corner activates workspaces on the host. That can give rise to some interesting Russian-doll screens:
Where you have similar operating systems between host and guest, I find it’s worth setting up different desktop backgrounds, so it is clear which environment you’re in. In practice, the tool-bars will generally have different contents, so I’ve not really found this to be a problem.
It’s not often I need to access VirtualBox settings, but if this is required I can float the mouse in the bottom-centre of the screen, and a pinnable menu will slide into view.
Back-up
One of the great advantages to full system virtualisation is being able to restore a whole system easily, but of course this is only as good as your last back up. A good solution here is to make it easy and, if possible, automatic. I’ve not set this up yet, but I expect a weekly script that does the following is feasible:
- Clone a VM using VirtualBox’s console tools (likely possible even if the VM is running)
- Check a backup drive is available to the host machine
- Copy the clone to the backup drive
- Delete anything older than the last five clones on the back-up drive
- Run md5sum over the local and remote clones for security
I found that copying a 37G file over USB2 took around 13 minutes (excluding hashing time), achieving around 50M/sec. Over USB3 (and especially to external SSD) I estimate this would take around three minutes!
Security
There are several features of this project that are intended to improve security, on top of the inherent safety of separating tasks into different virtual machines.
Firstly, I’ve used full disk encryption on the host drive. This means that, if someone was to try reading the disk directly, all the virtual guests are effectively encrypted, even though they were installed without the encryption option. The benefit of full encryption is clear: if you lose your laptop or it is stolen, then you’ll have the hassle of replacing it, but your confidential data will not spill out as a result (and hopefully you took a backup). Whilst I do recommend this setting, be absolutely sure you can remember your pass-phrase, as there is no hope of recovering anything if this is forgotten. (Incidentally, it is often better to write it down in disguised form than to try to memorise it).
I was worried that virtual machine performance would be adversely affected by host encryption, but — perhaps aided by the SSD drive — operational speed is excellent. LAMP applications work appreciably faster than the Mac (admittedly that has a lower spec) and large applications like GIMP and NetBeans start up in a few seconds.
When downloading software manually (Linux distros, VirtualBox, NetBeans) it is good practice to look up their checksums and ensure you have a match before proceeding. Whilst it is possible that a download could be turned into a malicious one at the point of its being downloaded (e.g. by a public wifi provider) the odds of someone being able to modify a checksum on the related website is nearly zero (NetBeans serve their hashes over SSL, making them even harder to tamper with).
For host and guest OS updates from a trusted repository, these do not need any further consideration with regard to security, as far as I know. As long as the installation image was trusted, it will have included the means to ensure new updates are correctly digitally signed. Since Linux is open-source software, I suspect it would be hard to inject vulnerabilities here without hash discrepancies being discovered by the community, especially given the number of nodes in their update networks.
For software that is not trustworthy (such as the conferencing software I mentioned earlier), users should have a policy of running this in a separate virtual machine. For that reason, it is worth having a spare fresh guest to hand, so it can be rolled back at the earliest opportunity.
I’m taking the view that it is not advisable to browse the web in the host, since browsing should take place within the security isolation of a guest. With that in mind, I removed the Firefox icon from the host’s launcher. On the rare occasions I need it, I start Firefox from a console, and use NoScript to offer additional protection.
Further improvements
At present, if I need to run something like Skype, I would do this in a virtual machine for security. However, this would prevent Skype’s user interface from being integrated into my usual working environment. The solution here might be to use a container in a guest; I don’t know how well that would run, but it’s worth a try. That will almost certainly use LXC, although a variety of approaches are available (someone’s got it working in Docker, yay).
I’ve not tried getting host hibernation working; I suppose it might be useful if I was caught with a low battery, and didn’t wish to shut down properly. Although I’m experiencing a crash when saving machine states in VirtualBox, at present I just sleep the laptop, and plug it in when it needs charging (I didn’t need to hibernate the Mac in several years of using it, so this isn’t immediately on my radar).
Given the concerns raised by closed-source software, and to support software freedom generally, it would be great if an open-source BIOS could be installed. However, I am not yet sure I am brave enough to re-flash this laptop while it is working fine!
Conclusion
I am now using the laptop day-to-day, since it is more than stable enough, despite some VirtualBox hiccups. There’s a few things OS X did that I need to replicate in my guests, but the trade-off is more than acceptable: I’m now using a significantly more secure computing environment, the performance has improved, and it’s on hardware that is mostly a joy to use. I would be pleased if this project encourages anyone else to try the same – please let me know your experiences in the comments.